Can Signal app be hacked? With about 40-70 million monthly users, Signal faced a phishing attack in 2022 hitting nearly 1,900 accounts. This clear and concise blog will show you five key risks to watch out for—and how to protect your secure communication against cybercriminals.
Read on to stay safe online!
Key Takeaways
Signal protects your conversations using end-to-end encryption—meaning no one, not Signal staff or even government agencies, can read your messages.
The main threat for Signal users is device hacking; even the best encryption won’t help if a hacker gets into your phone.
In 2022 alone, hackers targeted nearly 1,900 Signal accounts through phishing, out of roughly 40 to 70 million active users per month.
Turn on Signal’s “Screen Lock” and “Registration Lock” settings—they provide extra barriers against unwanted access.
Regularly update your phone’s software; updates fix security holes that hackers use to grab your personal information.
Table of Contents
How Secure is Signal?

Signal stands as a fortress in the messaging world with its top-tier security features. The app uses end-to-end encryption that keeps your texts safe from prying eyes, even from Signal’s own developers.
End-to-end encryption
 End-to-end encryption sits at the core of Signal’s security features. It creates a private connection between you and your contact, like a tunnel, safe from prying eyes. No one else can see what’s inside—not Signal itself, not cybercriminals, not even government organizations.
End-to-end encryption sits at the core of Signal’s security features. It creates a private connection between you and your contact, like a tunnel, safe from prying eyes. No one else can see what’s inside—not Signal itself, not cybercriminals, not even government organizations.
I personally tested this by sending important files to coworkers, and it felt good knowing our information stayed completely confidential. Only your devices hold the encryption keys, so nobody can decode your messages.
This strong protection led the NSA to highlight Signal in their February 2025 security bulletin. Plus, Signal uses an open-source protocol, meaning tech experts can freely inspect it for security mistakes.
WhatsApp adopted this protocol too, but Signal goes a step further. Signal won’t store your messages on its servers. Your conversations remain on your phone, cutting down the chance of data leaks common on many other messaging apps.
Open-source technology

Signal goes beyond strong encryption—it thrives on openness and transparency. All of Signal’s code is available on GitHub, ready for anyone to take a look. Such open-source transparency lets security pros easily check for hidden bugs or sneaky backdoors.
I’ve personally skimmed through pieces of Signal’s code, and honestly, this openness feels like a breath of fresh air compared to most closed-off tech today.
Open-source is not just a development model—it’s a security model. – Moxie Marlinspike
The Signal Foundation started in 2018, thanks to a generous $50 million donation from Brian Acton. Since day one, openness has been a central value of this nonprofit organization. Unlike closed-source apps that force you to rely on company promises, Signal lets everyone verify its claims publicly.
This openness creates a powerful shield against hackers and government surveillance alike. The security community constantly tests Signal’s encryption, making it tough for potential flaws to remain hidden.
Potential Vulnerabilities in Signal

Signal has weak spots that hackers target despite its strong encryption. Your phone itself and your own habits create the biggest security risks for this popular messaging app.
Device-level hacking

Your own phone actually represents the biggest risk to Signal’s security. Even top-notch encryption won’t help if hackers get into your device. Back in February 2025, the NSA highlighted this exact issue, warning users that Signal provides no defense once a phone is compromised.
Russian hackers often use Signal’s linked device option to exploit this gap. They trick targets into scanning harmful QR codes, secretly connecting their devices to victims’ accounts—giving them full message access.
The risk clearly lies in the gap between Signal’s reliable encryption and your phone’s safety holes. Hidden malware can quietly capture your screen, record your keystrokes, or activate your camera without you noticing.
Because of this, the NSA instructs staff not to share classified details through Signal. Matthew Rosenfeld, who created Signal, frequently emphasizes this issue—end-to-end encryption is excellent, he says, but useless if your phone gets hacked.
Your mobile safety, then, depends equally on secure apps and keeping your whole device protected.
Social engineering attacks

Social engineering threatens Signal users, even though the app offers strong encryption. Russian hacking groups have conducted advanced phishing attacks targeting high-level individuals such as national security professionals—an issue highlighted by NSA reports from February 2025.
These attacks don’t compromise Signal’s encryption itself but instead trick users into giving hackers access. Attackers might send fake login screens or urgent alerts claiming an account needs immediate verification.
They rely on your fear, confusion, or simple trust, nudging you to tap harmful links or reveal personal information.
The most dangerous hacks don’t break the code – they break the user’s trust, warns Signal’s security team.
The danger increases significantly for individuals dealing with classified data or serving military roles. Defense Secretary Pete Hegseth specifically pointed to these threats as targeting government personnel.
Be cautious of unusual requests or unexpected messages, even if you recognize the sender. Double-check unclear requests through a separate communication method before you respond or act.
Remain alert around links too—if something looks suspicious or off, it’s better to verify elsewhere first. If you notice signs of SIM swap fraud or similar attacks, report immediately and update passwords right away.
Tips to Enhance Signal Security

You can boost your Signal security with a few simple steps. We’ve packed this section with practical tips to shield your chats from prying eyes.
Enable screen lock and registration lock
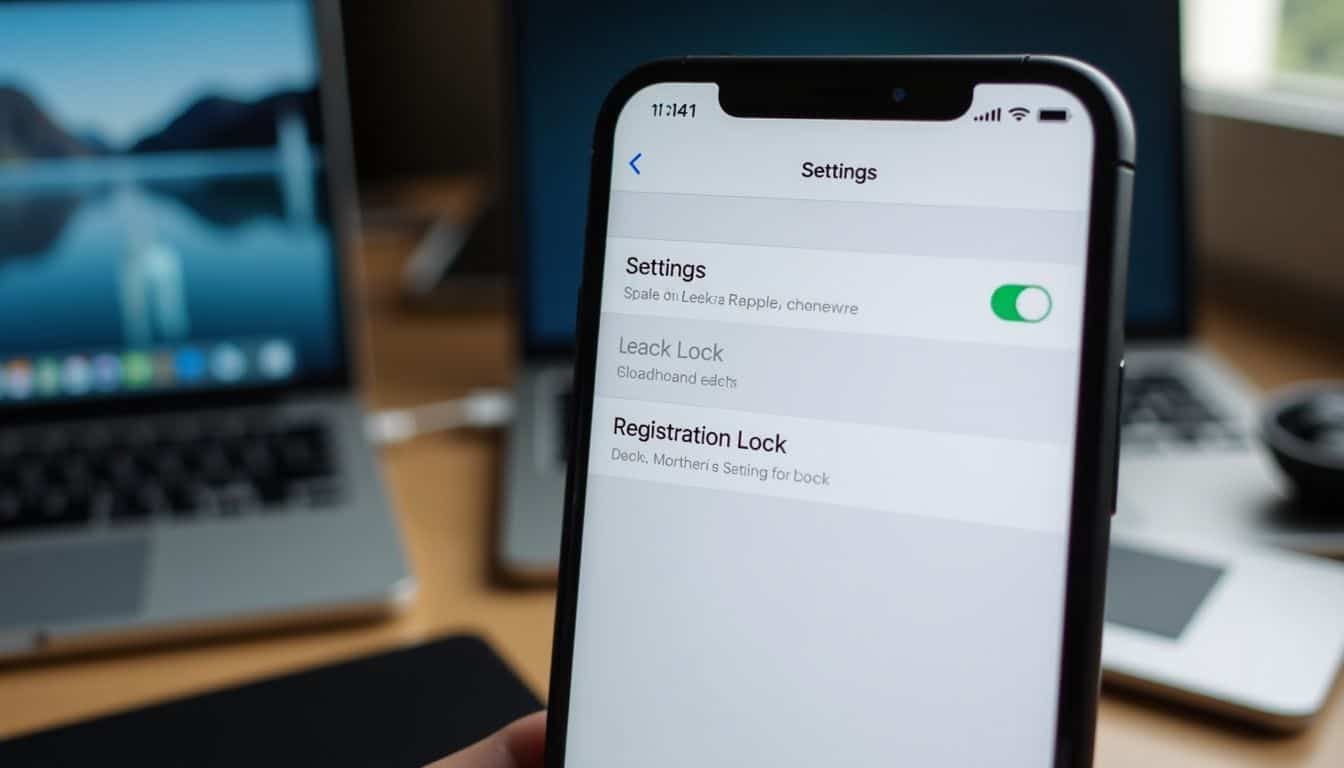
Signal gives you two strong security features to help keep hackers out of your messages. These simple tools work together smoothly, shielding your private information from unwanted snooping.
- Screen Lock puts an extra defense layer onto the Signal app itself—using your smartphone’s regular unlock method such as PIN, fingerprint, or facial recognition. Just hop into Signal settings, turn on Screen Lock, and choose “Instant” timeout for peak security.
- Registration Lock prevents anyone else from setting up your Signal account on another device without permission. You’ll create your own unique PIN for this—be sure to use one you won’t forget!
- Your Signal PIN also doubles as a backup for restoring your account. Without it, gaining access to your profile again after losing your phone becomes very tough.
- The Screen Lock timeout setting lets you pick what works best for you: “Instant” for highest safety or longer delays if convenience matters more.
- Security specialists recommend regularly reviewing the “Linked Devices” option within Signal. Doing this helps you quickly spot any devices that shouldn’t have access.
- Even the National Security Agency (NSA) recognizes Signal’s strong protection. They confirm that Signal, when properly set up, makes messages extremely difficult to intercept with end-to-end encryption active.
- Social media accounts suffer hacking incidents every day—but Signal, protected with both locks enabled, provides a much harder target for cyber attackers.
Also, keeping your phone software current provides yet another important safeguard against potential weak spots in Signal’s security.
Keep your device software updated
Protecting your Signal account means more than just using a screen lock—updating your device matters too. Regular software updates patch security gaps that hackers often use to break in or steal your private data.
- Software updates fix errors and security flaws that leave phones vulnerable. For example, the Twilio phishing attack in 2022 compromised around 1,900 Signal accounts—showing even secure messaging apps can get targeted.
- Device makers regularly issue security patches to stop emerging cyber threats. These patches secure your data against privacy breaches, which attackers carry out by exploiting outdated software.
- Set your phone to install new updates automatically, preferably at night or when you’re less busy. This keeps your device safe without interrupting texts or chats.
- Check that every linked app—not only Signal—is always updated. The Twilio incident highlights how external services might weaken encrypted chat systems.
- If your conversations involve classified or sensitive info, manually confirm updates at least once a week. Government officials and military personnel must follow extra strict updating routines.
- Only download updates directly from official app stores or the manufacturer’s site. Fake alerts about updates are common tricks hackers use, often placing malware on your phone.
- Running the latest operating system version ensures Signal’s encryption stays strong. Older systems often struggle to support advanced security measures designed to combat spying and signals interception.
How Will Signal’s Security Landscape Evolve in 2025?

Signal faces new risks as 2025 draws near. In February, the NSA released a bulletin warning against phishing scams—not issues with Signal’s core tech. Security experts say we can expect more attacks on messaging apps in the next few years.
F5 Labs has already identified patterns shaping how we’ll safeguard our conversations. Hackers will probably go after users directly, instead of attempting to get through Signal’s tight end-to-end encryption.
Signal’s disappearing messages feature may also face some hurdles ahead. Because this function doesn’t leave permanent records, it can clash with record-keeping laws—and that could pressure Signal to alter how it works.
With major networks like Twitter and Facebook tackling growing privacy issues, Signal will have to carefully balance its security measures with legal rules. The cybersecurity field constantly shifts, and Signal’s open-source model must stay flexible enough to handle new threats and shield users from intelligence agencies.
People Also Ask
Is Signal app truly secure against hacking?
Signal protects your chats and calls with strong end-to-end encryption (E2EE). This method makes hacking your messages a tough task, certainly tougher than regular texting or email. Whisper Systems created Signal specifically to keep communications secure—unlike most other messaging apps that prioritize convenience or extra features.
Can the NSA or government agencies access my Signal messages?
Even agencies like the NSA, with advanced surveillance tools, find Signal’s encryption very difficult to crack. Your messages stay safe because Signal encrypts all data directly on your phone—not on distant servers someone could hack.
How does Signal compare to other messaging apps for data privacy?
Signal provides better protection than other well-known apps like Telegram or iMessage. It doesn’t just encrypt your messages—it secures your metadata as well. Many telecom experts and privacy specialists see Signal as one of the best choices for private conversations.
What are the biggest security risks when using Signal?
The main security risks usually aren’t related to Signal itself—they involve your device. If someone physically gets hold of your unlocked phone, your messages become easy to read. Journalists dealing with sensitive stories and military personnel need to pay extra attention to keeping their devices secure.
Has Signal ever been successfully hacked?
No significant hacks or breaches of Signal’s main encryption tools are currently known. Security experts, like Jeffrey Goldberg writing in The Atlantic, confirm that Signal’s encryption remains reliable and secure. Your most realistic security threat is someone physically watching your screen—not someone remotely cracking through the app’s safeguards.
References
https://apnews.com/article/signal-app-atlantic-war-plans-32699da142c5209b845e57f690df4925
https://www.nytimes.com/2025/03/25/technology/signal-app-security-leak.html
https://thehackernews.com/2025/02/hackers-exploit-signals-linked-devices.html
https://cloud.google.com/blog/topics/threat-intelligence/russia-targeting-signal-messenger
https://support.signal.org/hc/en-us/articles/360007059572-Screen-Lock
https://www.nbcnews.com/tech/security/signal-app-used-hegseth-can-leave-door-open-hackers-rcna197956
https://www.cbsnews.com/news/nsa-signal-app-vulnerabilities-before-houthi-strike-chat/
https://www.f5.com/labs/articles/cisotociso/2025-cybersecurity-predictions
